
Overview
Because threats and vulnerabilities are constantly evolving, we strongly advise to perform vulnerability scans on a regular basis. IT security starts by facing threats and vulnerabilities!
To assist you in this process, we provide a vulnerability assessment solution in the form of a virtual appliance. It scans an unlimited number of IPs, as often as you like, and identifies the vulnerabilities and configuration issues that hackers use to penetrate your network.
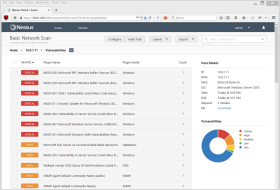
Scanning options
Our appliance performs non-credentialed remote scans, credentialed local scans - for a deeper analysis of assets - and offline auditing on a network device’s configuration. It supports a wide range of operating systems, databases, (web) applications, and network devices.
Threat detection
It can also scan for viruses, malware, backdoors, hosts communicating with botnet-infected systems, known/unknown processes, as well as for malicious content on websites. Sometimes more effective than a traditional antivirus system!
Validation
In addition, the results of the vulnerability scanner can be imported in an automated GUI-based penetration testing tool. This will validate potential issues by auto-exploiting the vulnerabilities! We provide a custom training to teach you the concepts of vulnerability scanning and validation.
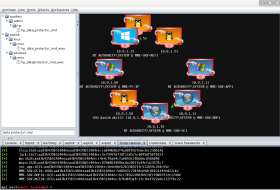
Related
Included
- Unlimited IP/asset scanning
- Internal and external scanning
- Software update subscription
- Installation and configuration
- Custom training course
- Automated validation tool

More info
The appliance can be bought with an annual software update subscription, or rented on a weekly basis.
To request a price quote or for more information, please fill out the form below.
